Graylog
Detect failed Windows updates with Graylog
This alert is even simpler than the bruteforce check.
Microsoft stores successful Windows updates with the event ID 43, 44 or 19. All we need to do is create a filter for all other IDs.
Updates are stored in Winlogbeat in the winlogbeat_winlog_event_data_updateTitle field.
The search input is done on the Winlogbeat input as source:
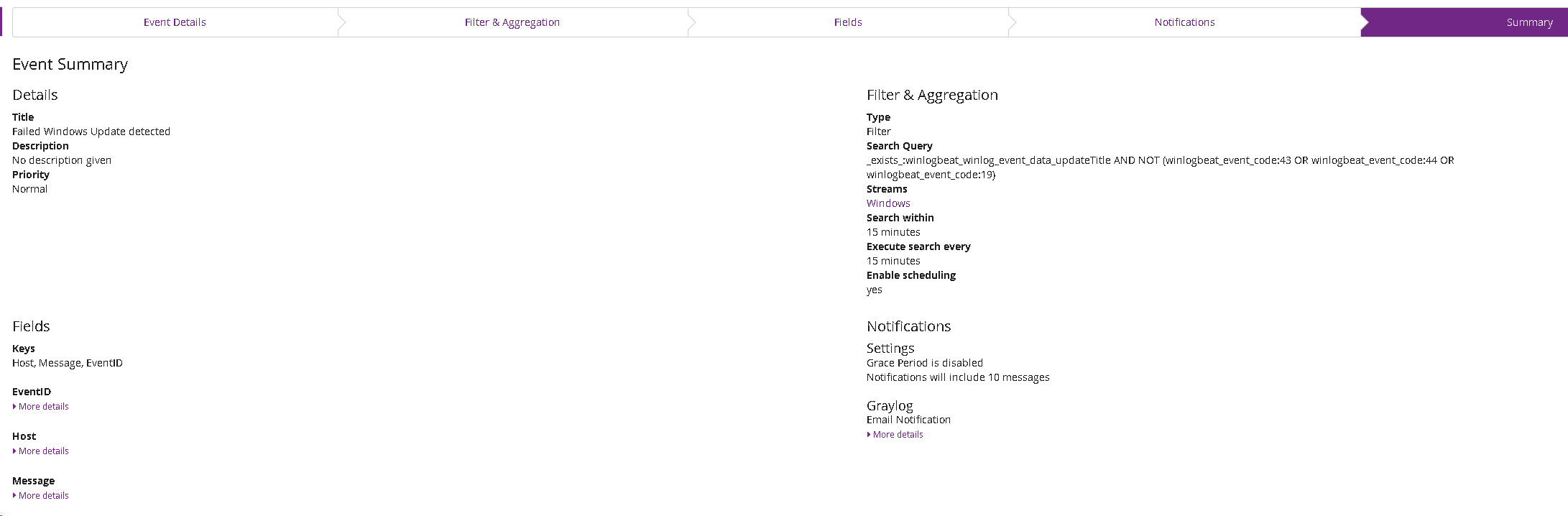
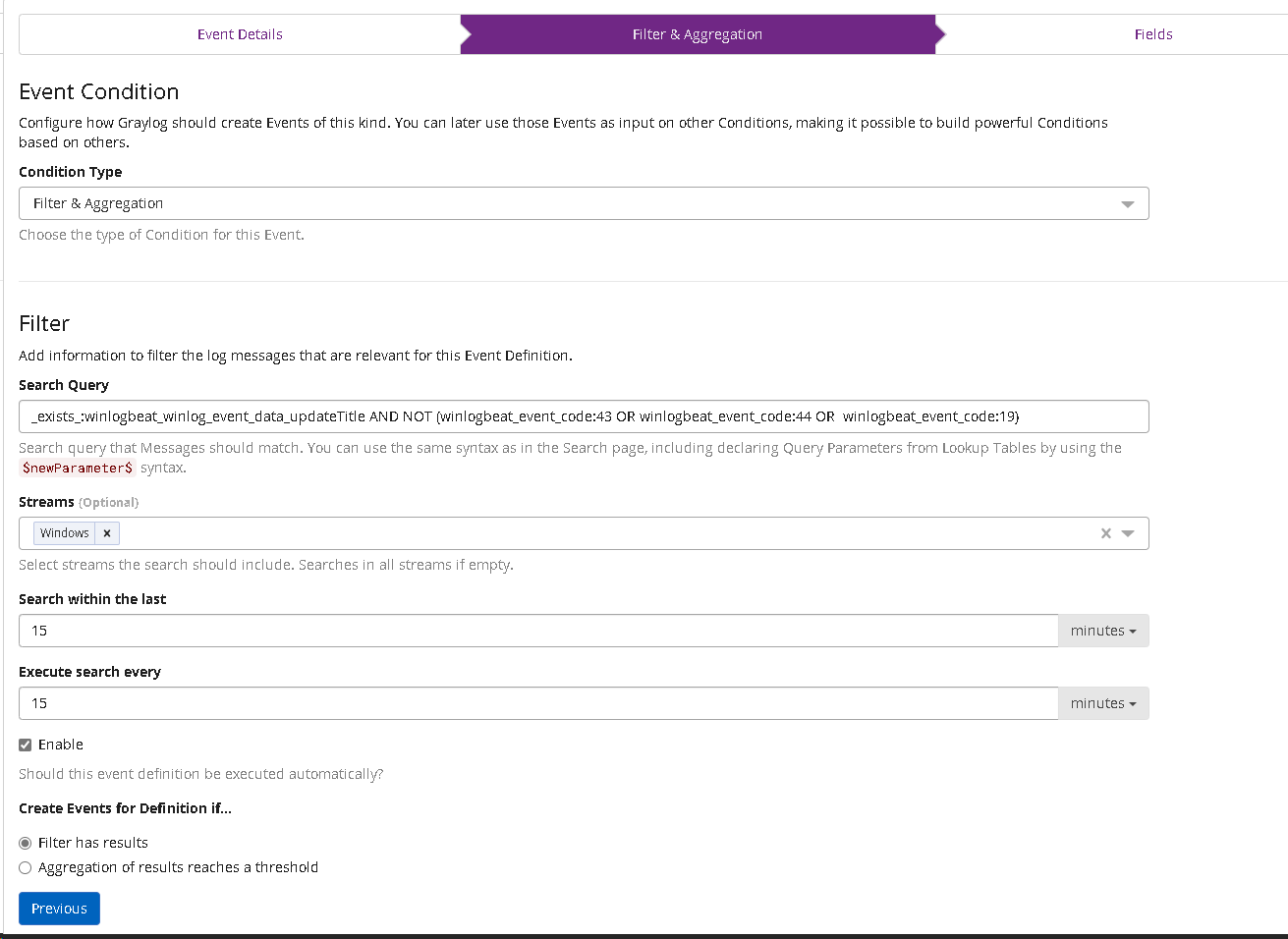
_exists_:winlogbeat_winlog_event_data_updateTitle AND NOT (winlogbeat_event_code:43 OR winlogbeat_event_code:44 OR winlogbeat_event_code:19)Go to alerts and create a new event.
Create a filter using the input from above:
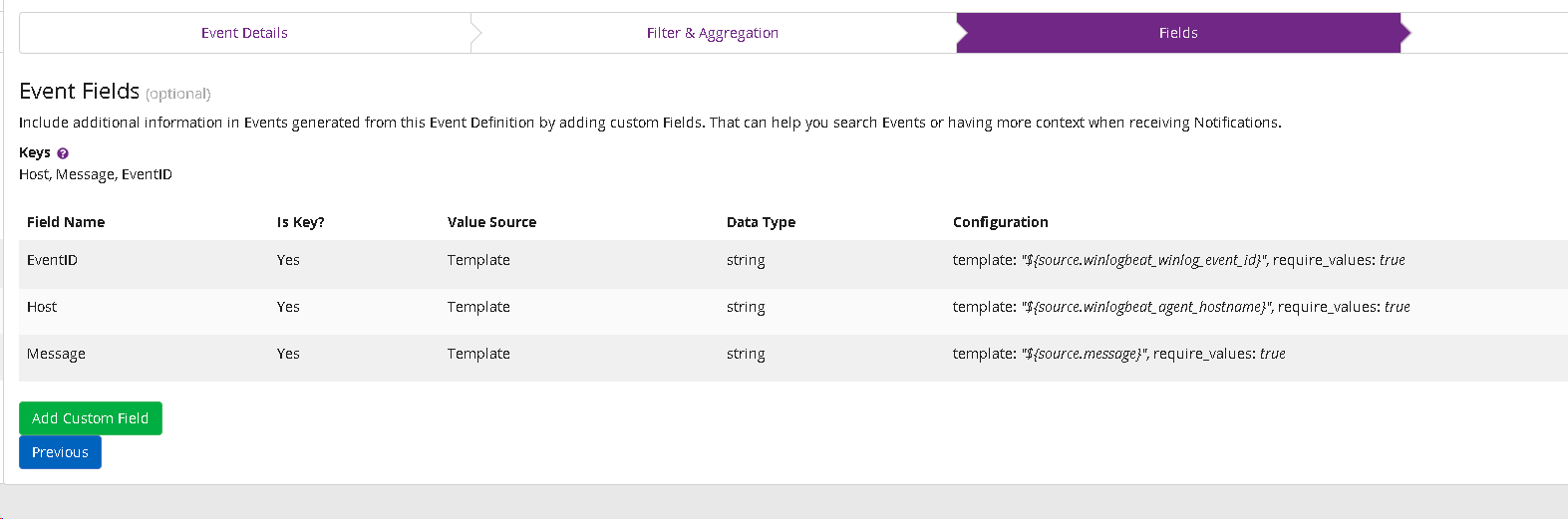
Add fields for alert output:
Edit the notification channels as desired (you are free to choose whether you want to be alerted by email or otherwise). Your summary should look like this: