
Send encrypted logs to Graylog (Part 2: Windows machines)
We now need to copy the Shadow Root CA from the first part to the Windows machines as well.
In case you can't remember: The required certificate is located on the Graylog server under /usr/local/share/ca-certificates/.
Import your shadow root CA
You will need administrator rights for the following steps.
Since Windows feels like it changes with every update and version and settings are found in other places, we use the time-honored Microsoft Management Console (MMC).
For those who don't know what that is. MMC is Microsoft's own management tool that is installed by default.
I assume that you have transferred the Shadow Root CA to the Windows machines.
Click on the start button and type "mmc". Run MMC as administrator.
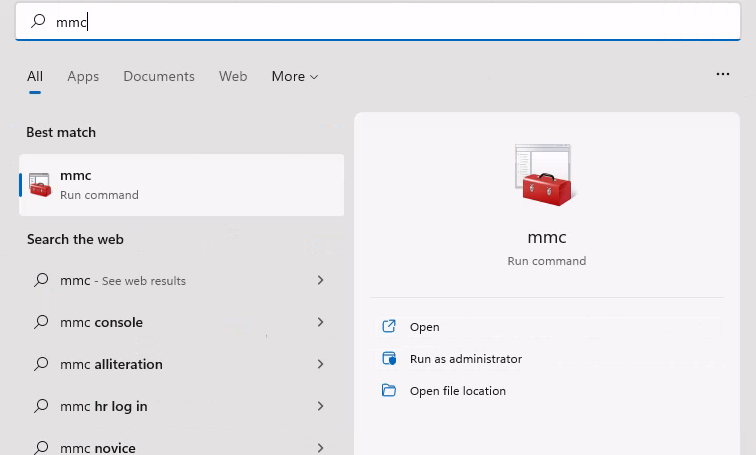
Open the "file" tab and click on "Add/Remove Snap-in".
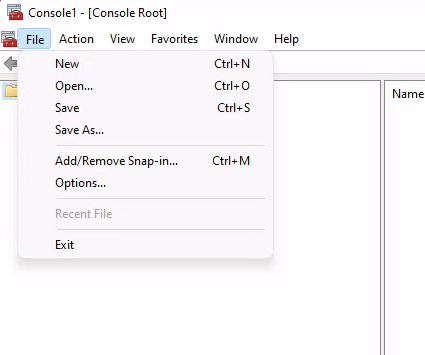
Open "Certificates" Snap-in and check the "Computer account" box.
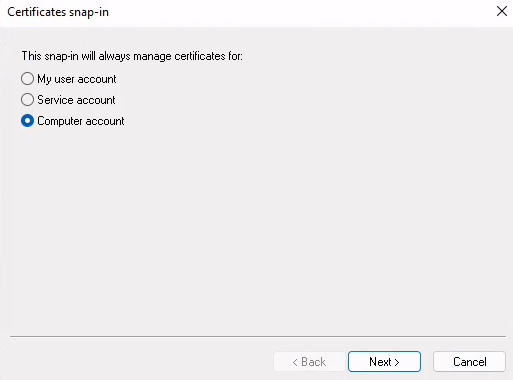
Click "Next" and select "Local Computer" in the next step.
Finish the setup and and click on ok in order to close the snap-in selection window.
Your console root should look like this:
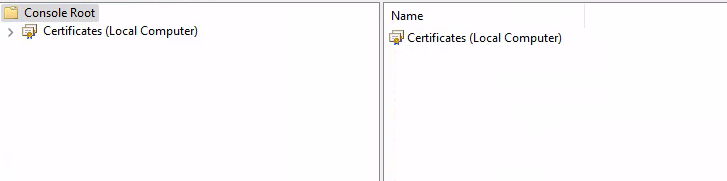
Open the certificate manager by double-clicking on "Certificates (Local Computer)". Click on "Trusted Root Certification Authorities" in the next screen.
After clicking on "Certificates" you should see a number of already installed certificates.
Here we import our self created one.
You can import via the form field "Actions" on the right side. The task is a bit hidden in the nesting. Use the screenshot below for orientation.
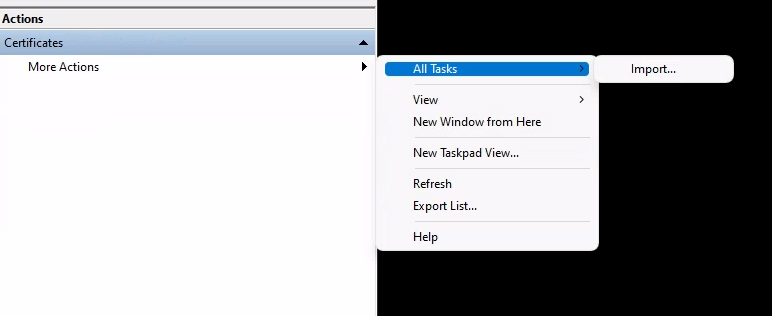
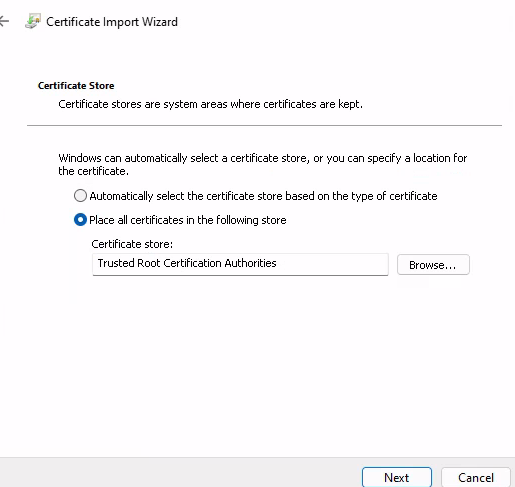
The import with the wizard is self-explanatory. Here it is important that you do not select the automatic import, but "Place all certificates in the following store: Trusted Root Certification Authorities".
After successful import you can close the MMC window. We do not need it anymore.
Create a new Beats input in Graylog
Create a new input Use the following settings:
bind_address:
0.0.0.0
no_beats_prefix:
false
number_worker_threads:
2
override_source:
<empty>
port:
5044
recv_buffer_size:
1048576
tcp_keepalive:
false
tls_cert_file:
/etc/graylog/ssl/graylog.crt
tls_client_auth:
disabled
tls_client_auth_cert_file:
<empty>
tls_enable:
true
tls_key_file:
/etc/graylog/ssl/graylogPKCS8.key
tls_key_password:
********Install and configure Winlogbeat
Download winlogbeat from elastic and unpack it.
At the time of writing, there is Winlogbeat 8. If you are still using version 7, upgrade beforehand because there were some breaking changes with version 8.
Create a new folder winlogbeat in C:\Program Files and move the unzipped files there.
Add your Shadow CA to your keystore
Since our cert is selfsigned, it's not enough to import it to your Windows host machine.
Create a new directory "ssl" within C:\Program Files\winlogbeat and copy your Graylog CA cert to this folder.
Open a Powershell window in administrator mode and create a keystore:
cd 'C:\Program Files\winlogbeat\'
.\winlogbeat.exe keystore createAdd your cert to your keystore:
winlogbeat.exe keystore add .\ssl\graylog-ca-root.crtWinlogbeat asks for a value that you can choose freely. I use Graylog.
Enter value for .\ssl\graylog-ca-root.crt:
Successfully updated the keystoreCheck your keystore:
C:\Program Files\winlogbeat> .\winlogbeat.exe keystore list
.\ssl\graylog-ca-root.crtOpen winlogbeat.yml in C:\Program Files\winlogbeat. Remove Elasticsearch Output and activate Logstash Output. Change your hostaddress.
# ------------------------------ Logstash Output -------------------------------
output.logstash:
# The Logstash hosts
hosts: ["YOURGRAYLOGIP:5044"]
# Optional SSL. By default is off.
# List of root certificates for HTTPS server verifications
# removed ["/etc/pki/root/ca.pem"]
ssl.certificate_authorities:
# Certificate for SSL client authentication
# ssl.certificate: "/etc/pki/client/cert.pem"
# Client Certificate Key
#ssl.key: "/etc/pki/client/cert.key"Install winlogbeat:
C:\Program Files\winlogbeat> PowerShell.exe -ExecutionPolicy UnRestricted -File .\install-service-winlogbeat.ps1
Security warning
Run only scripts that you trust. While scripts from the internet can be useful, this script can potentially harm your
computer. If you trust this script, use the Unblock-File cmdlet to allow the script to run without this warning
message. Do you want to run C:\Program Files\winlogbeat\install-service-winlogbeat.ps1?
[D] Do not run [R] Run once [S] Suspend [?] Help (default is "D"): R
Status Name DisplayName
------ ---- -----------
Stopped winlogbeat winlogbeatCheck if the connection is established:
PS C:\Program Files\winlogbeat> .\winlogbeat.exe test output
logstash: 192.168.131.15:5044...
connection...
parse host... OK
dns lookup... OK
addresses: YOURGRAYLOGIP
dial up... OK
TLS...
security: server's certificate chain verification is enabled
handshake... OK
TLS version: TLSv1.3
dial up... OK
talk to server... OK